You register or login to your digital marketing agency’s account online. Let's say on LinkedIn, Facebook, Twitter, or Email. Even your web server, cloud server, database server, website backend, and Google analytics. You think of a simple password and easy to remember.
You think “iloveyou” or “mamamia” or “123456789” as your password. These passwords are extremely vulnerable to brute force attacks and dictionary attacks. We also know that creating a password like “I8^%@JKW825*” is a very easy task but remembering it, is way difficult! 😭
Imagine, you created a digital marketing blog today. And next day you have no access to it, simply someone has guessed your password, logged in and change it without your permission!
Your passwords allow you to your kingdom. So, you're probably worried about what's the best practice to build a good password protection. The one to protect your accounts from these cybercriminals.
If you use one of the passwords mentioned here:
it's probably time to update it. The most common passwords on the Internet are detailed in a new report from Trustwave. Password1 takes the lead over Welcome1 and P@ssword. More information can be found in the Independent:
Recent reports have spoken:
- 155.8 million records were exposed from the vulnerable database in 2020.
- 95% of breaches are caused by human error.
- The funniest and dangerous one, there is a hacker attack every 39 seconds.
These reports tell us to be more dynamic in protecting our online accounts than ever. If changing it after three months was your habit, then you should consider minimizing the duration. Maybe every month or every week or even when you hear a breach occurred.
Doing so, you need a brain same as that of a Microsoft datacenter😊 or else you’ll forget your passwords.
The rules in this article will guide us to create passwords and never forget them. In the easiest way for us but most difficult for a hacker.
Before diving into the ways to protect your accounts, let’s first understand the methods that hackers might use to obtain your passwords:
1. Brute force attack
An intruder tries to guess every combination in the book. The intruder automates software to attempt as many variations as possible in as short a period as possible. There have been some unfortunate improvements in the development of this technology. Generally, something less than 12 characters is vulnerable to cracking. Therefore, the length is important. The longer the password the better.

2. Phishing
It is when cybercriminals want to deceive, intimidate, or pressure you. Usually by social engineering techniques in order to unintentionally do anything they like. Phishing emails can warn you (falsely) that there is something wrong with your credit card account. You will be led to click a link that will take you to a false website that looks similar to your credit card company. The website might require you to enter your credit card details and password.
My colleague once said, “Once you are online, never trust anyone! Even yourself!”.

3. Dictionary Attack
😂don’t mind the above image. The hacker is essentially targeting you with a dictionary.
A brute force attack attempts every combination of symbols, numbers, and letters. But a dictionary attack tries a pre-arranged list of words you'd find in a dictionary.
You can only survive a dictionary attack if your word is wildly odd or if you use several words such as GlassZebraHouseWork. These multiple-words outsmart a dictionary attack.
💪💪CAUTION: 43% of cyber-attacks target small businesses (cybintsolutions.com/cyber-security-facts-stats). You need to keep your digital marketing agency’s employees on alert and safe. To keep your agency’s data, blogs, or website safe.
Now that we know how passwords are cracked, we can build solid ones that outsmart any threat. Your password is on the way to being unbreakable if it meets these five (8) simple rules.
The strong password anatomy
a. Do not be obvious.
Keep out of the clear and don’t be too honest. Never use sequential numbers or letters, and do not use a word "password" as your password for the sake of all cyber material. Come up with special one that do not contain any personal details, such as your name or date of birth. If you're chosen directly for a breach, the hacker would put whatever they know about you in their guess attempts.
b. Hide from brute force.
Should be long. This is the most significant aspect. Choose nothing less than 15 characters or more, if possible.
Using a blend of characters. The more letters (upper-case and lower-case), numbers, and symbols you combine, the stronger your password becomes. Also, it becomes more difficult to break it with brute force attacks.
Avoid making traditional substitutions. Login crackers are hooked to the regular substitutions. If you use TABLEPHONE or 7A8LEPH0N3, the brute force attacker breaks it with similar ease. Nowadays, spontaneous character positioning is more effective than common speech substitutions. Do not use unforgettable keyboard paths. As the aforementioned recommendation, do not to use sequential letters and numbers. Do not use sequential keyboard paths (like qwerty). They're among the first to be guessed.
c. Hide from a dictionary attack
The trick to stave off this form of attack is to ensure that the password is not just a single word. Many terms are going to complicate this tactic. Remember, these threats limit the potential number of guesses to the number of words.
Example: choosing a passphrase like "I want to play cricket for Bridging Technologies" and changing it at random with uppercase, numbers, or special characters: ‘! Want to PLAY CR!CK3T for T@nz@n!a?
d. The revised passphrase method
This is a multi-word expression system with a twist—choose bizarre and unusual phrases. Using proper names. Names of nearby companies, historical figures, other words you know in a foreign language, etc. A hacker might guess Quagmire, but he or she might find it ridiculously difficult to try to guess a decent example of a password like this: QuagmireHancockMerciDeNada.
e. Method of the sentence (I recommend this for those who cannot remember their passwords)
The idea is to think of a random sentence and use a rule to turn it into a password.
For example, taking the first two letters of each word in “The old man is my favorite uncle in South Tanga” would give you: TholmaismyfauninSoTa.
f. Use trusted password managers
A password manager is a piece of software that stores and manages a user's passwords. It is for different online accounts and security features. With the support of a master password, password managers store passwords in an encrypted format. They also provide safe access to all password details.
There are several different types of these managers. Each with its own encryption method, storage type, and additional features.
Example LastPass.
🔥🔥Pro Tip: With your digital marketing agency on the line, the safest storage is your brain. Use these managers only on generating new passwords.
g. Revise and change your passwords regularly.
A good password should have at least 12 characters. Include uppercase and lowercase letters, numbers, and special symbols, according to security experts.
Use a password generator (https://www.lastpass.com/password-generator), which can be found in most password managers. It quickly and easily generates a complex, strong password. Passwords are often exposed as a result of data breaches.
You should stop reusing yours across several sites and accounts and change them regularly.
h. Use 2F authentication.
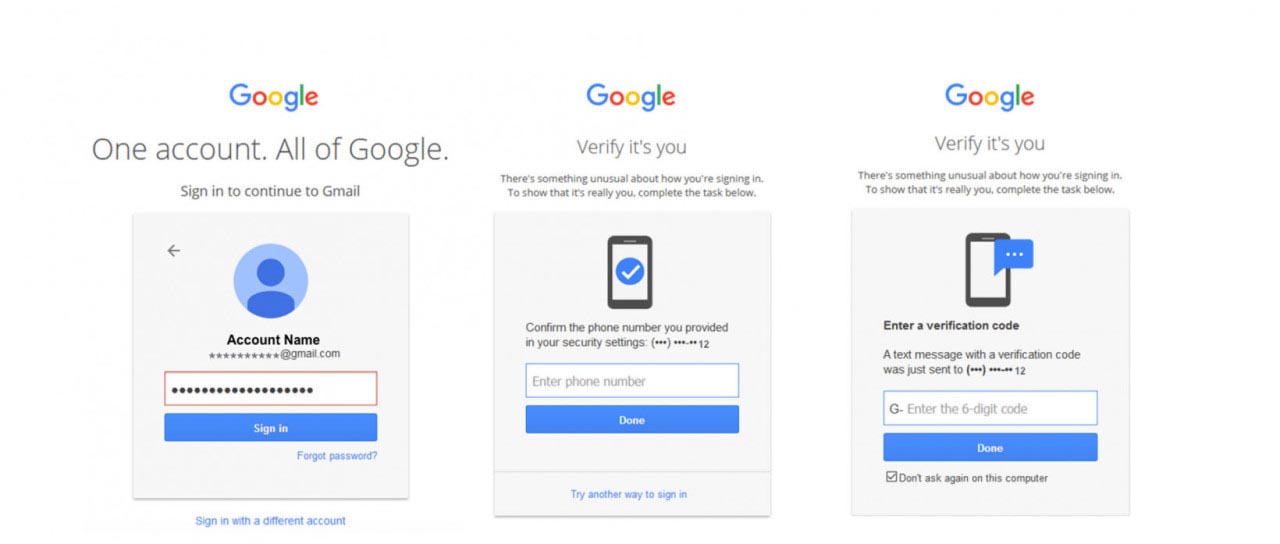
When an employee logs in for the first time from a new computer, they must enter a PIN sent to the account owner via an app, SMS, or email. It not only protects you from lost or stolen passwords, but it also ensures that the account owner is present when signing in on new or current devices.

I hope that you can create your password using these rules. Remember this, 8 rules are not enough, your habit also plays a crucial part in protecting your online passwords. Never do the following:
✔️Reusing your password
This is one of the most popular risks and severe vulnerabilities. It has little to do with software or apps and has everything to do with your habits. People try to remember different passwords for anything they deal with on a daily basis. Then they use the same one across multiple systems, apps, or even social media sites. The flaw is caused by a person's inability to remember dozens (or even hundreds) of passwords.
When one account is hacked, all other accounts that share the same password are also at risk. The more it is repeated, the more likely it is to be broken or stolen. If a website is hacked, hackers can try to gain access to other accounts by using the login details on other websites. As a result, rather than simply losing access to the one compromised account, you could find yourself dealing with a series of problems. These problems can have disastrous consequences for your privacy and online protection.
✔️Sharing your password
When you share it with someone else, they gain access to not only that account, but all of your other accounts that use the same password. Sharing them carries the risk of making your account even less safe.

Even if you trust the person to whom you offer your password, they cannot keep it safe. Or they may keep it on a compromised computer, exposing it to hacking and putting you, your accounts, and your personal information at risk. It's important that you're cautious about who you send your password to.
✔️Staying put
Have I been hacked? Is my account compromised? How will I know? These are most common questions you always ask yourself. Well, it is difficult to notice that you have been hacked. Although agencies or websites sometimes report that they've been hacked or they have had data stolen, they typically don't do so right away.
Avast Hack Check tells us that there are two ways to know that your account is compromised. One, identity theft and two, when you allow hackcheck to check your account.
Passwords can never be given out to anybody, including students, faculty, or employees.
🚩🚩Pro Tip: You can test if your password is strong enough using Kaspersky’s password check tool.
For the rest of your digital marketing security, password protection should consider:
- Installing a good Internet security program that provides proactive protection. The program has features against new threats rather than just antivirus protection.
- As soon as security updates are available, apply them to your operating system and applications. Don't put it off any longer! Turning on automatic course updates is beneficial.
- In untrusted emails or websites, do not click on links or attachments. To prevent being taken to a phishing site.
- Only create accounts to the websites you trust.
- Installing unknown or suspicious programs on your computer or mobile device is never a good idea.
- Before discarding documents that contain classified or personally identifying information, shred them completely.
So

Concerned about your digital marketing security? The importance of training your employees about how to handle strong passwords cannot be ignored. They will always do what makes their lives easier. That is, they will do so even though they are aware that their password protection is jeopardized.
Educate them with these simple 8 rules.
🧲🧲You can reach us through or make a short call on +255762110000.



